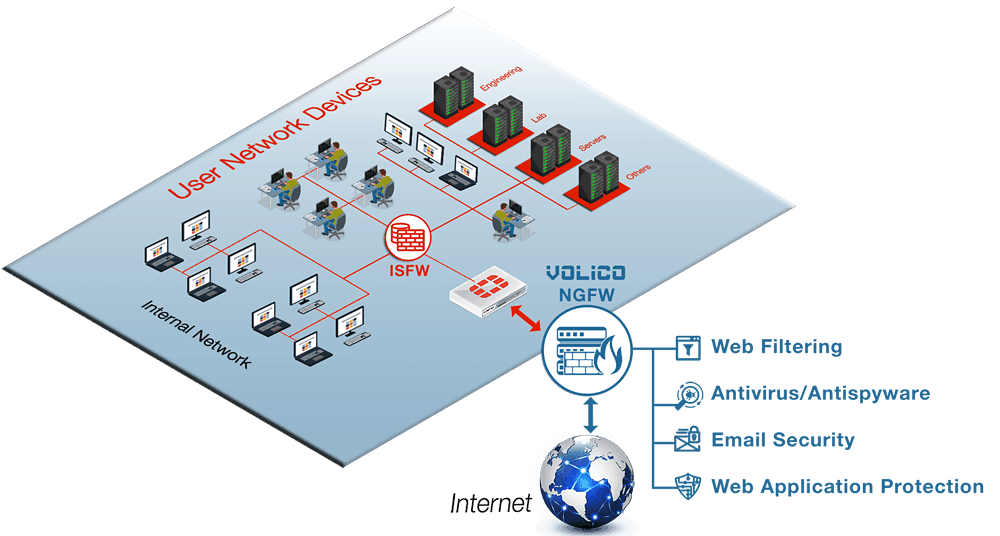
SolutionBase: Configuring remote access VPN connections in a back-end ISA firewall configuration | TechRepublic
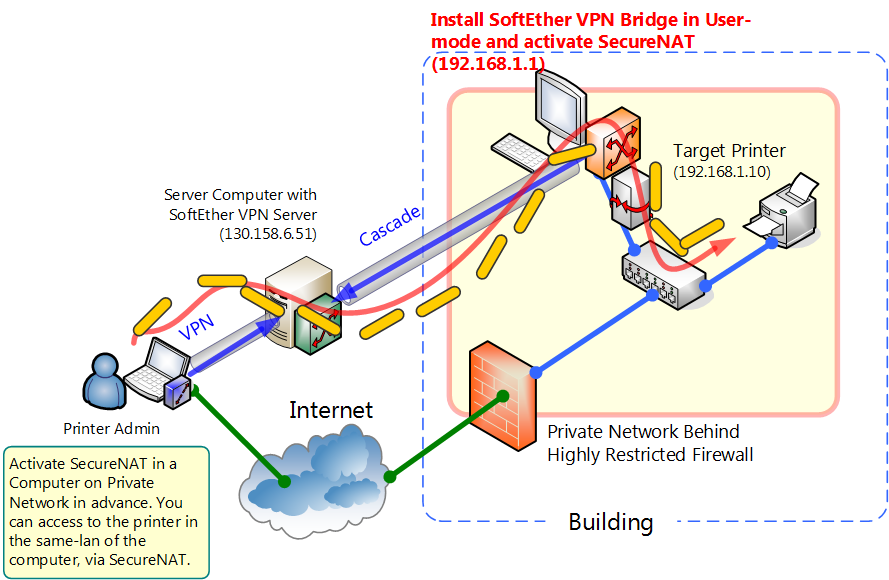
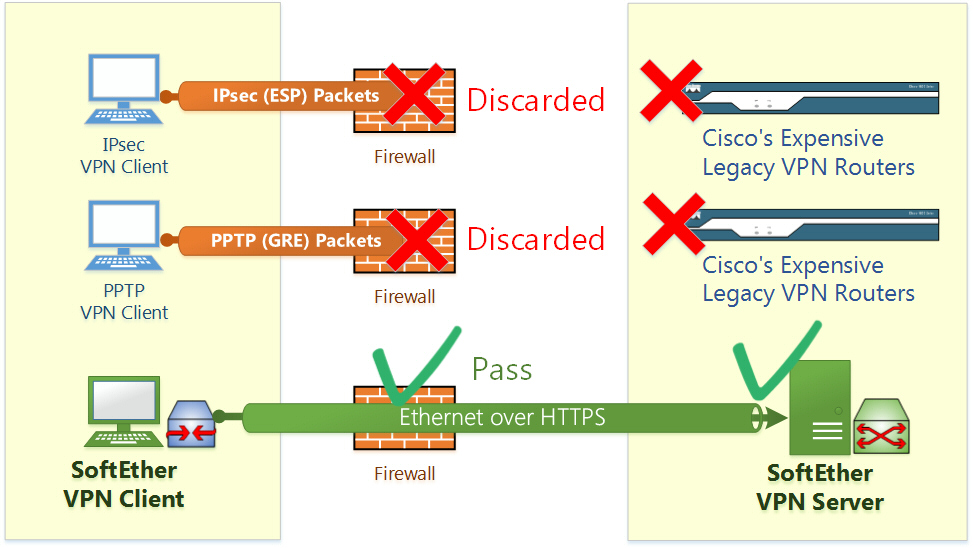
10.11 Exploit SecureNAT for Remote Access into Firewall without Any Permission - SoftEther VPN Project

Configuring VPN When Fortinet FortiGate Firewall Is Used_Virtual Private Network_Administrator Guide_HUAWEI CLOUD
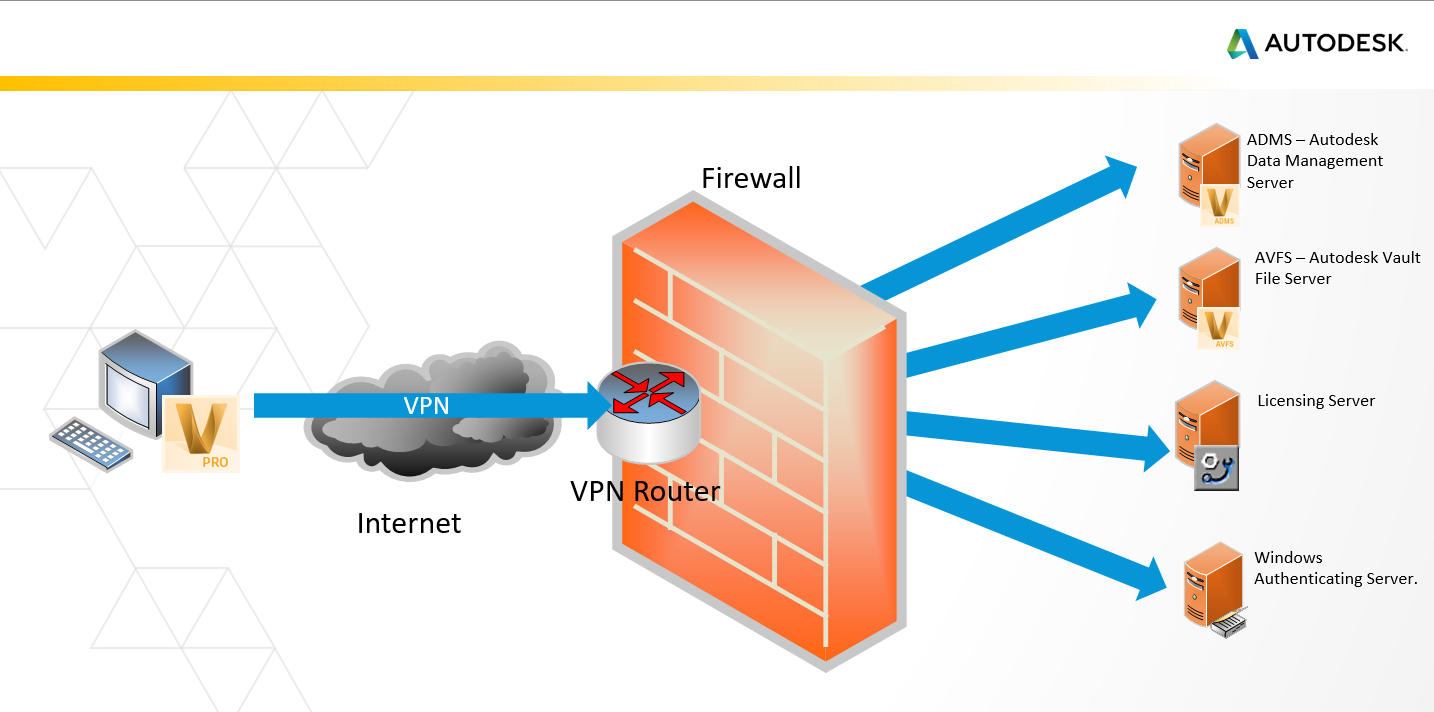
Troubleshooting client connections to Vault Server through a VPN (Virtual Private Network) or to the cloud | Vault Products | Autodesk Knowledge Network

VPNs and Firewalls : [Filtering packets, Firewalls, Internet, VPN server interface, L2TP, IPSec packets, over IPSec, packet filtering, Packet filters, L2TP over IPSec, PPTP, packets, VPN, PPTP connections, Layer Two Tunneling Protocol,
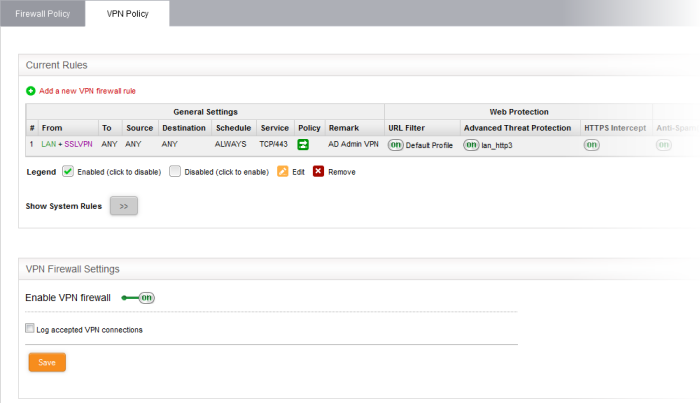

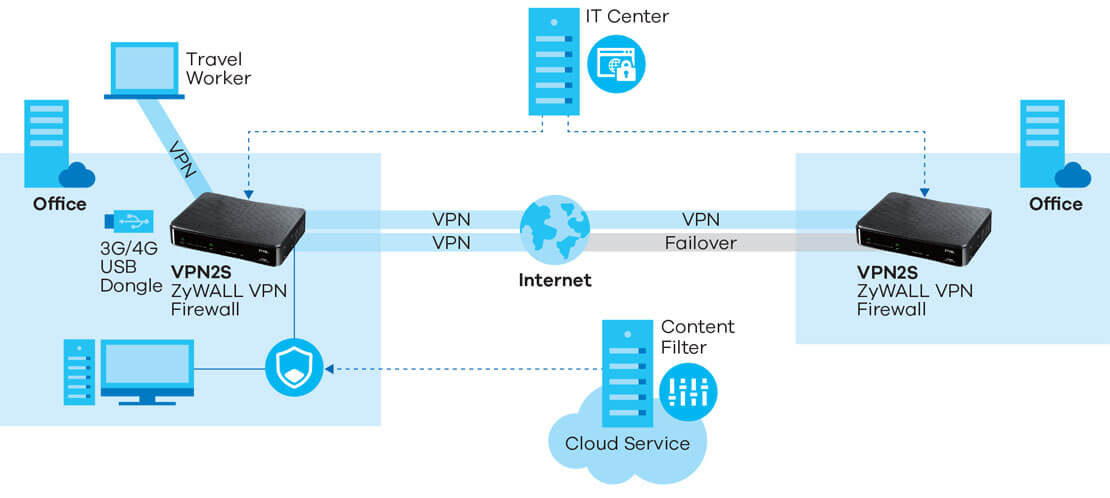


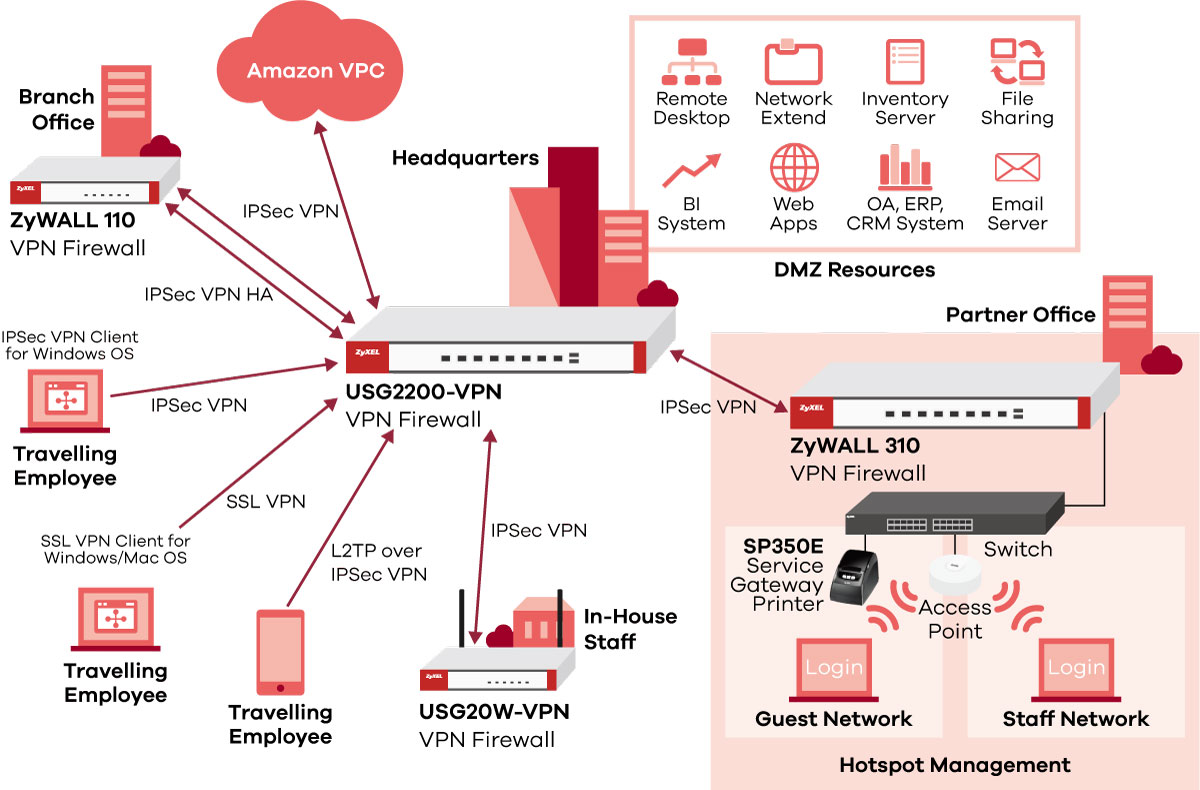
/ZyxelNextGenerationVPNFirewall-593075425f9b589eb472f995.jpg)

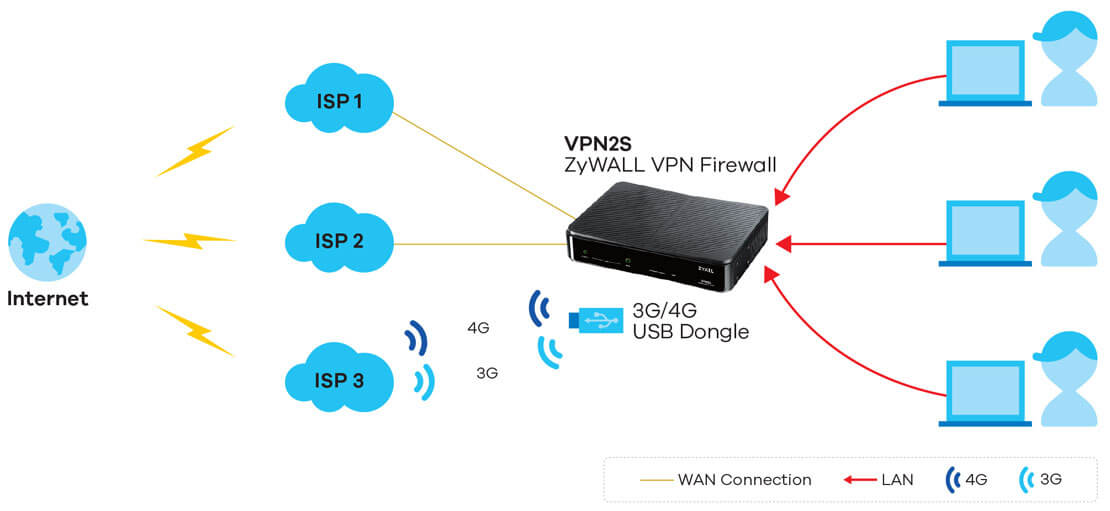

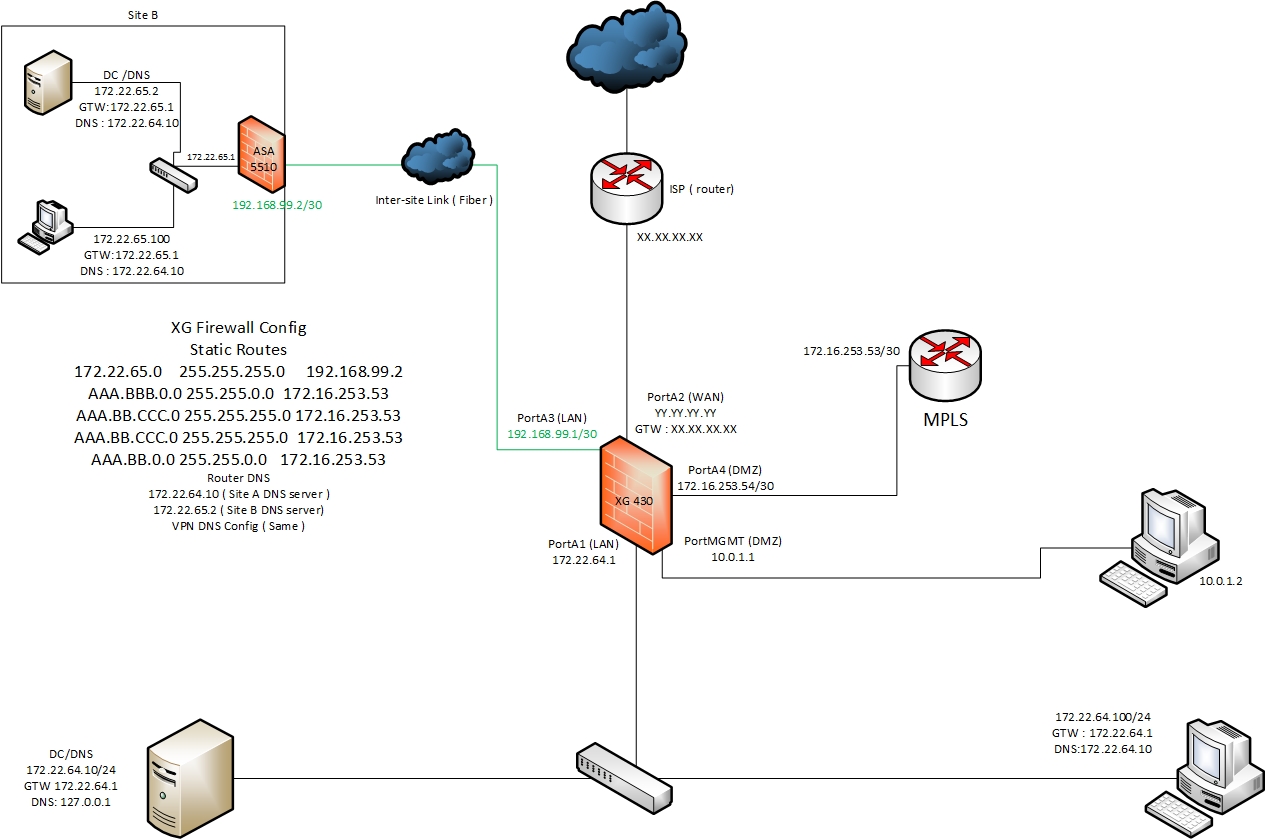
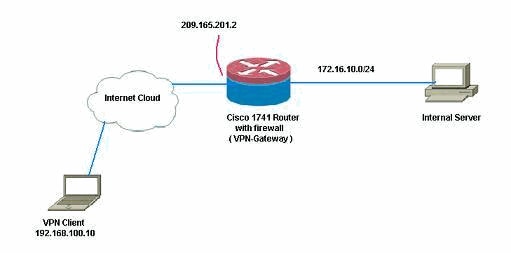
![VPN Design - Practical Network Scanning [Book] VPN Design - Practical Network Scanning [Book]](https://www.oreilly.com/library/view/practical-network-scanning/9781788839235/assets/3e6152d6-f614-4102-9c53-9b8387c97ea5.png)