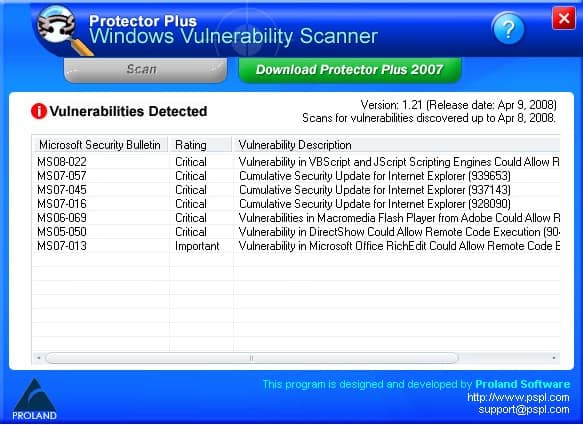
Built-in vulnerability assessment for VMs in Microsoft Defender for Cloud - Microsoft Tech Community

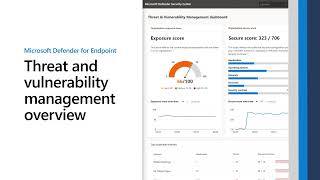
Microsoft's Threat & Vulnerability Management now helps thousands of customers to discover, prioritize, and remediate vulnerabilities in real time - Microsoft Security Blog

Help using the Microsoft Baseline Security Analyzer (MBSA) | Information Technology | University of Pittsburgh
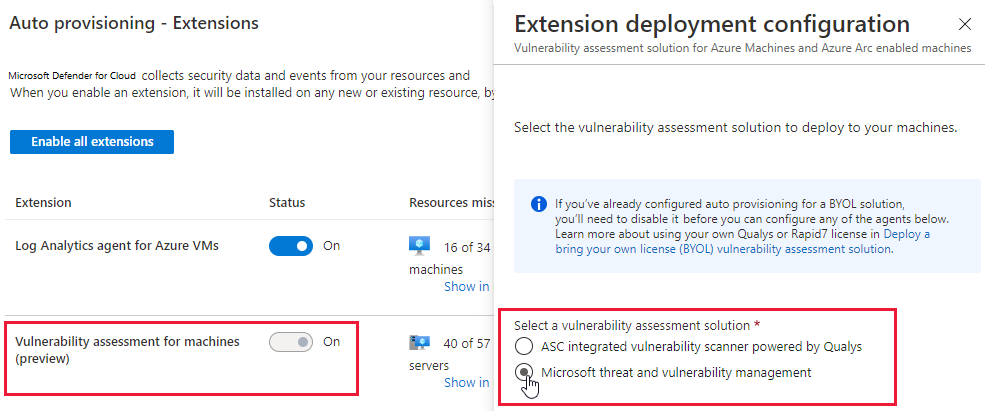
Configure Microsoft Defender for Cloud to automatically assess machines for vulnerabilities | Microsoft Docs

Microsoft's new security tool will discover firmware vulnerabilities, and more, in PCs and IoT devices | TechRepublic
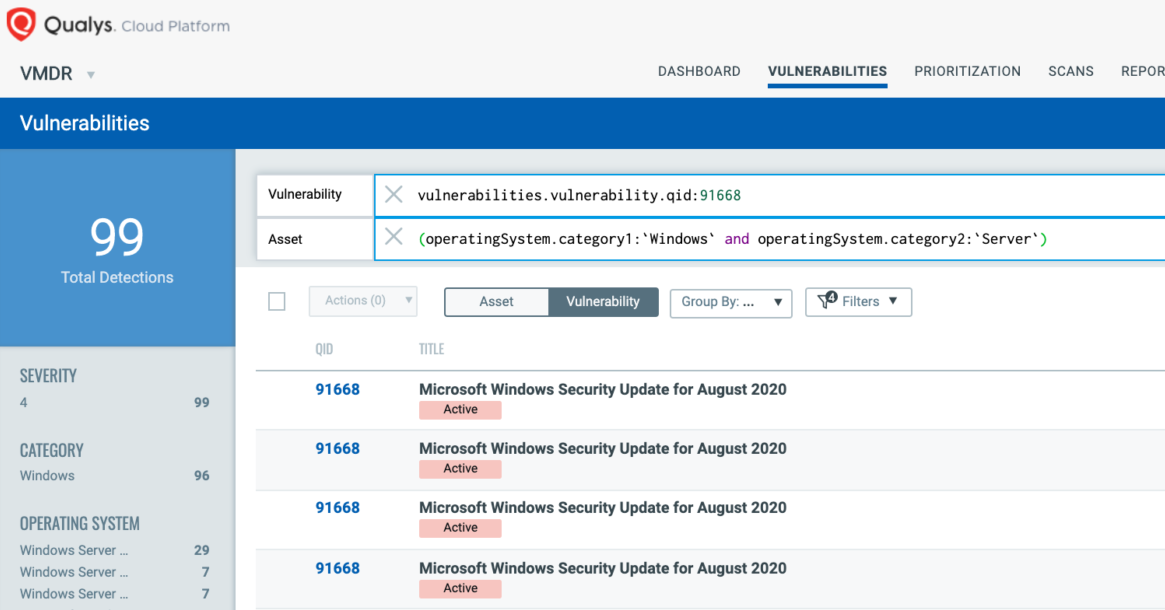
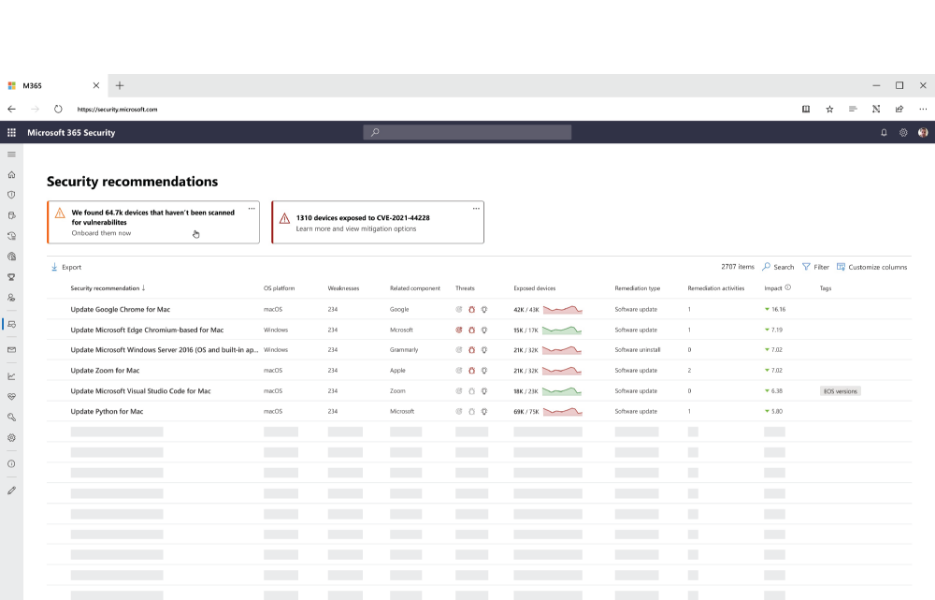
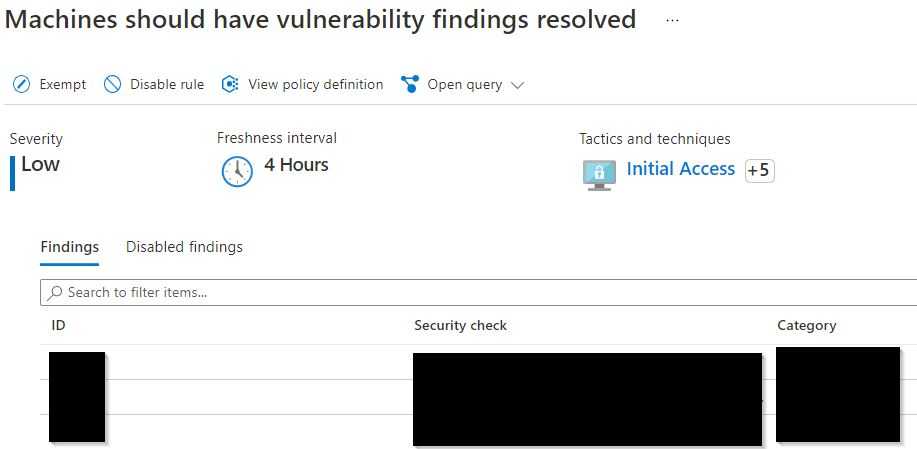


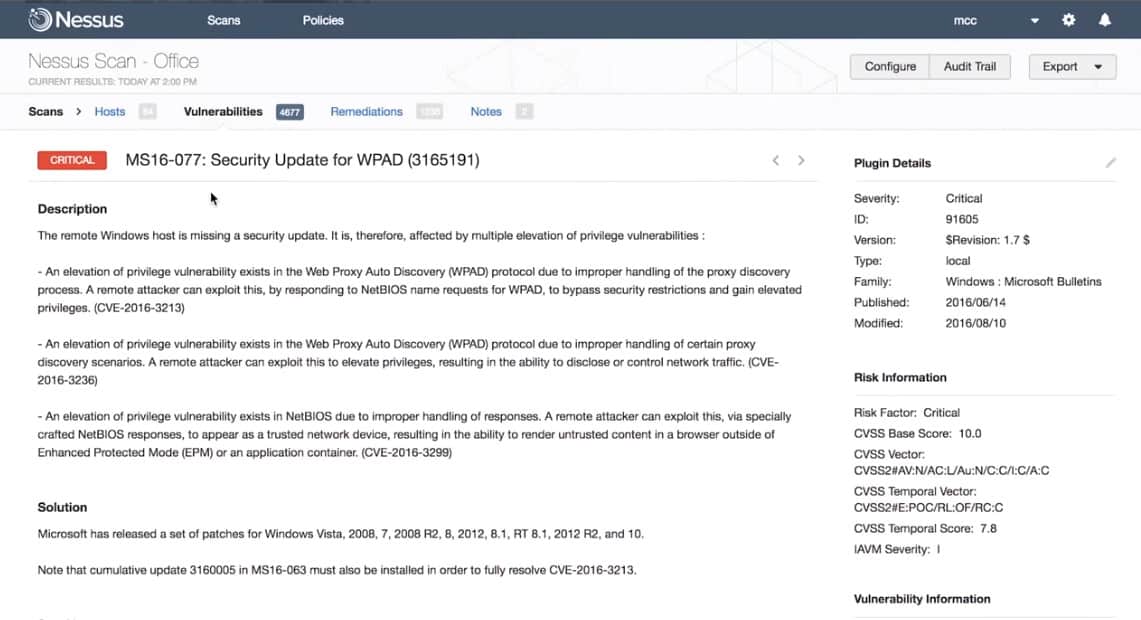

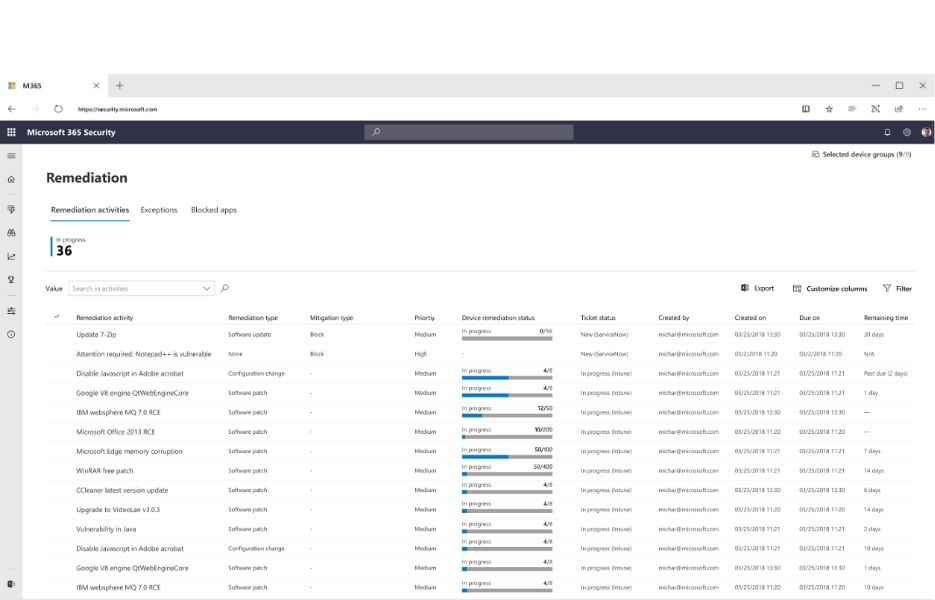

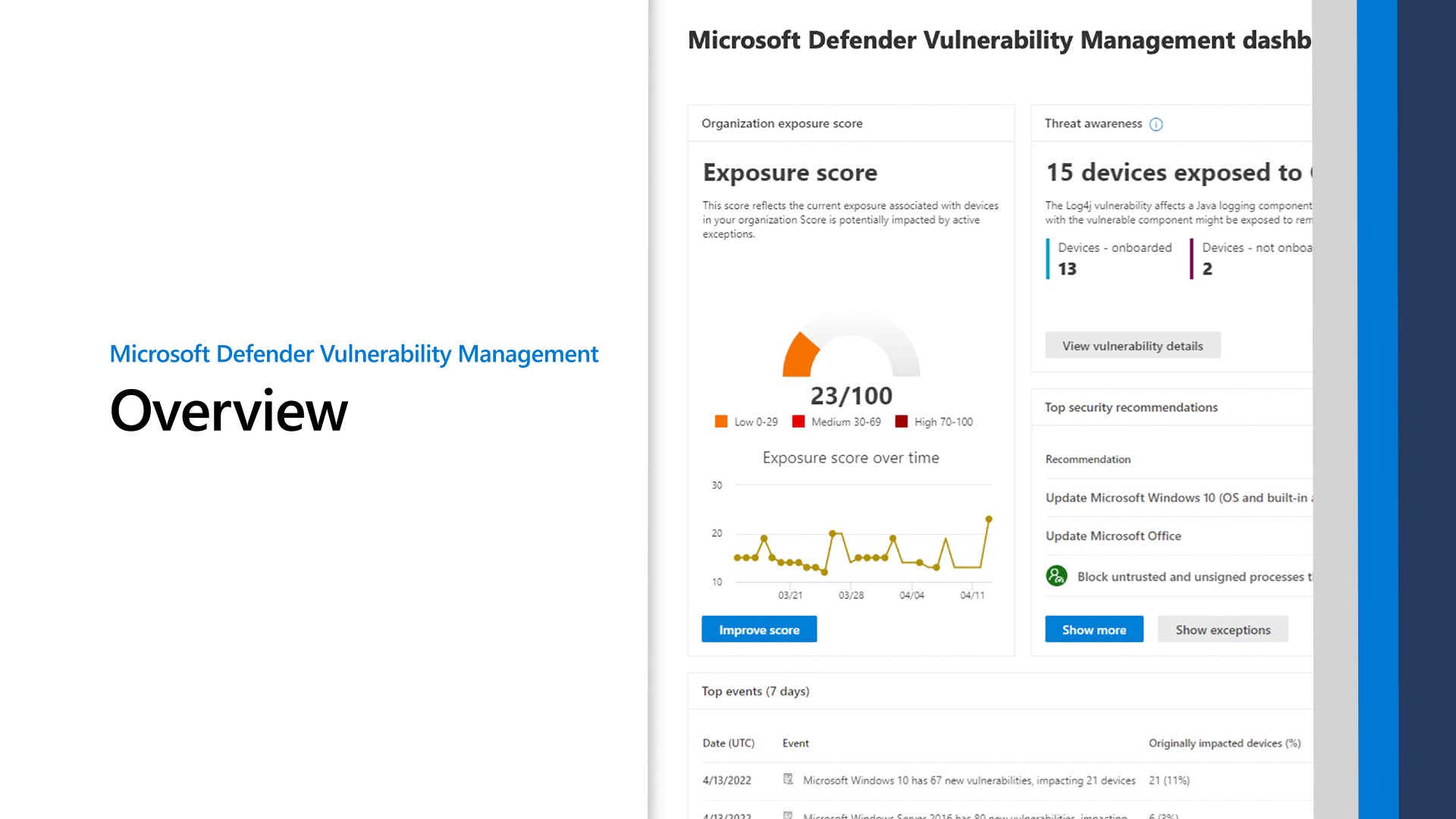
.png?width=1674&name=MicrosoftTeams-image%20(76).png)