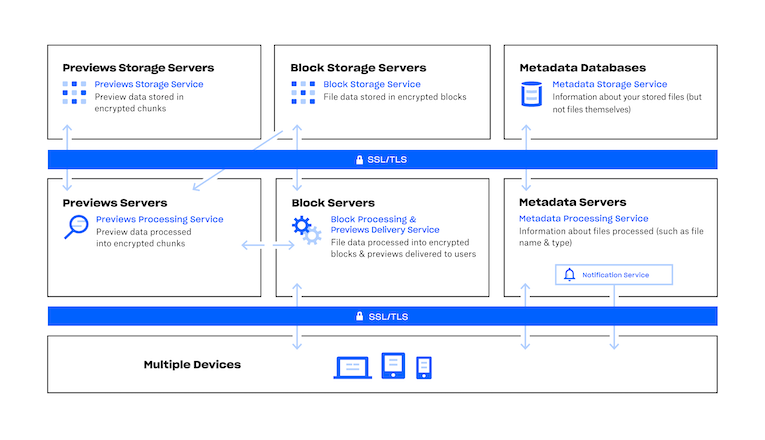
Block Design including the encryption (red box) and decryption (blue... | Download Scientific Diagram
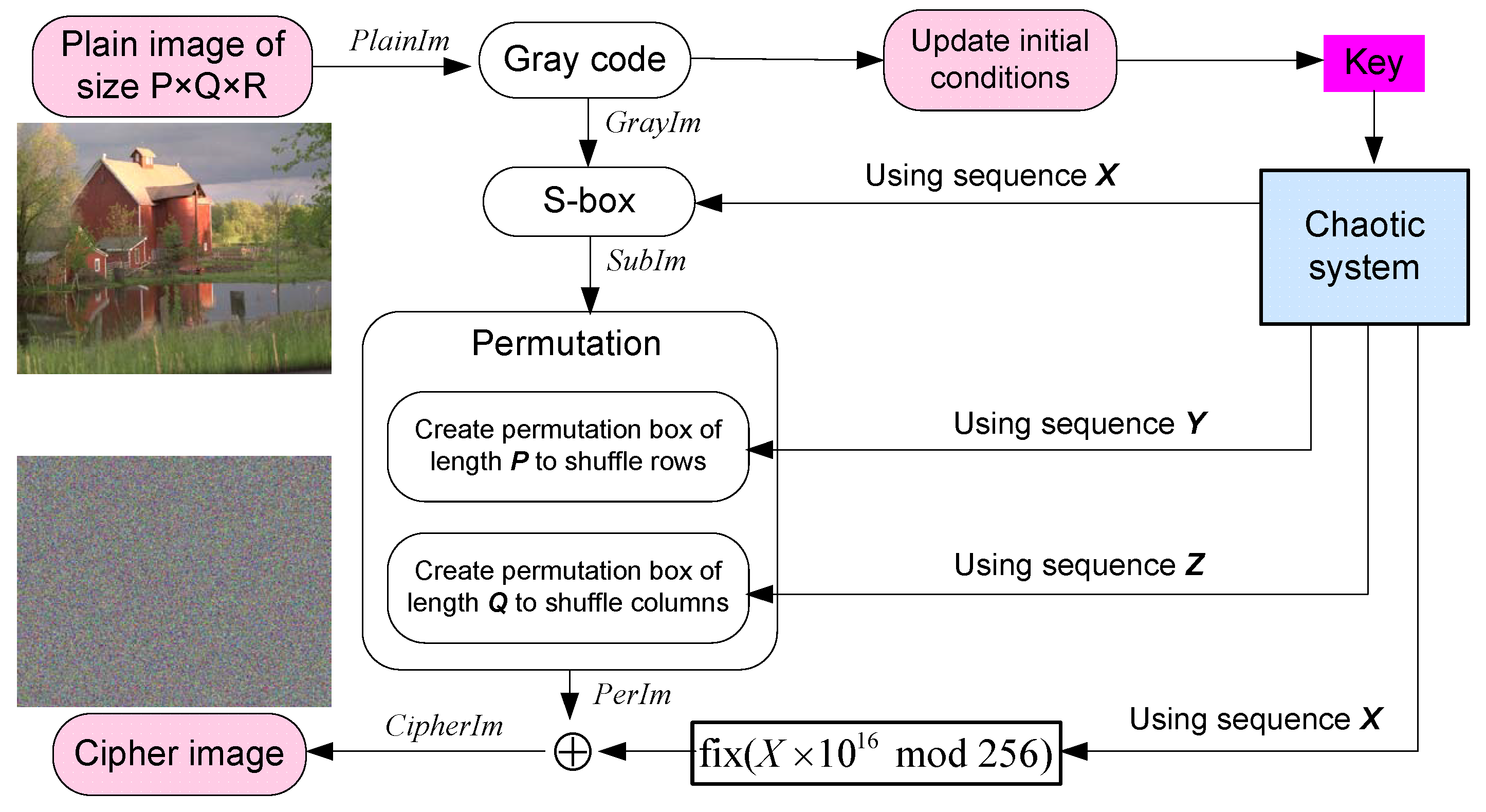
Electronics | Free Full-Text | Efficient Chaos-Based Substitution-Box and Its Application to Image Encryption | HTML
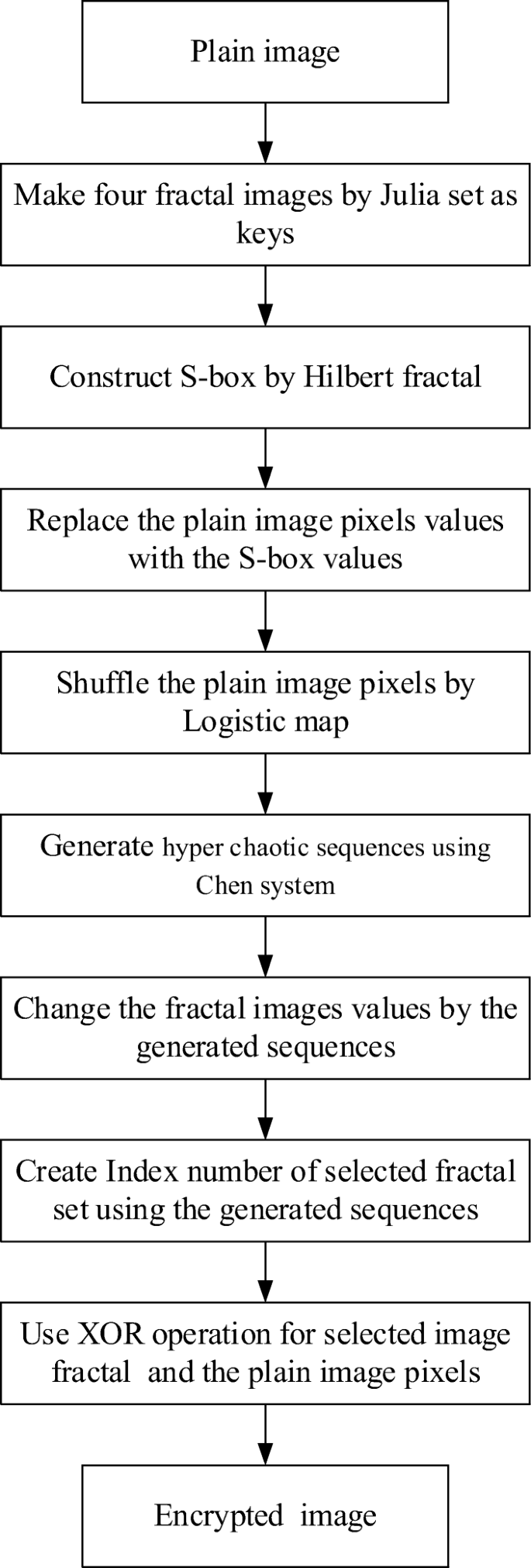
A novel color image encryption algorithm based on substitution box and hyper-chaotic system with fractal keys | SpringerLink
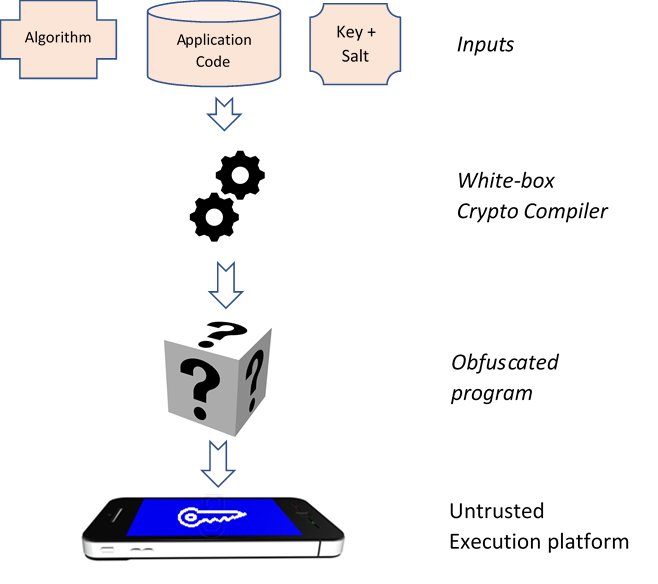
How White-box Cryptography is gradually eliminating the hardware security dependency | by Terugu Venkat | Engineering Ezetap | Medium







![PDF] WHITE-BOX CRYPTOGRAPHY : HIDING KEYS IN SOFTWARE | Semantic Scholar PDF] WHITE-BOX CRYPTOGRAPHY : HIDING KEYS IN SOFTWARE | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/370d9da733a85717974d09924ce3b3ca7a98c510/3-Figure2-1.png)




:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/3395694/Box_EKM_Encryption_Flow.0.png)